Ce sujet a été résolu
Post. 
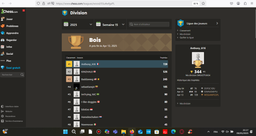
Division de bois.
 https://www.chess.com/leagues/wood/5Su4wfgsPL
https://www.chess.com/leagues/wood/5Su4wfgsPL
Division de pierre.
 https://www.chess.com/leagues/bronze/4tUGTFsN54
https://www.chess.com/leagues/bronze/4tUGTFsN54
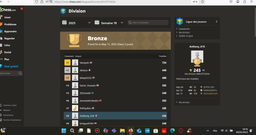
 https://www.chess.com/leagues/bronze/4tUGTFsN54
https://www.chess.com/leagues/bronze/4tUGTFsN54
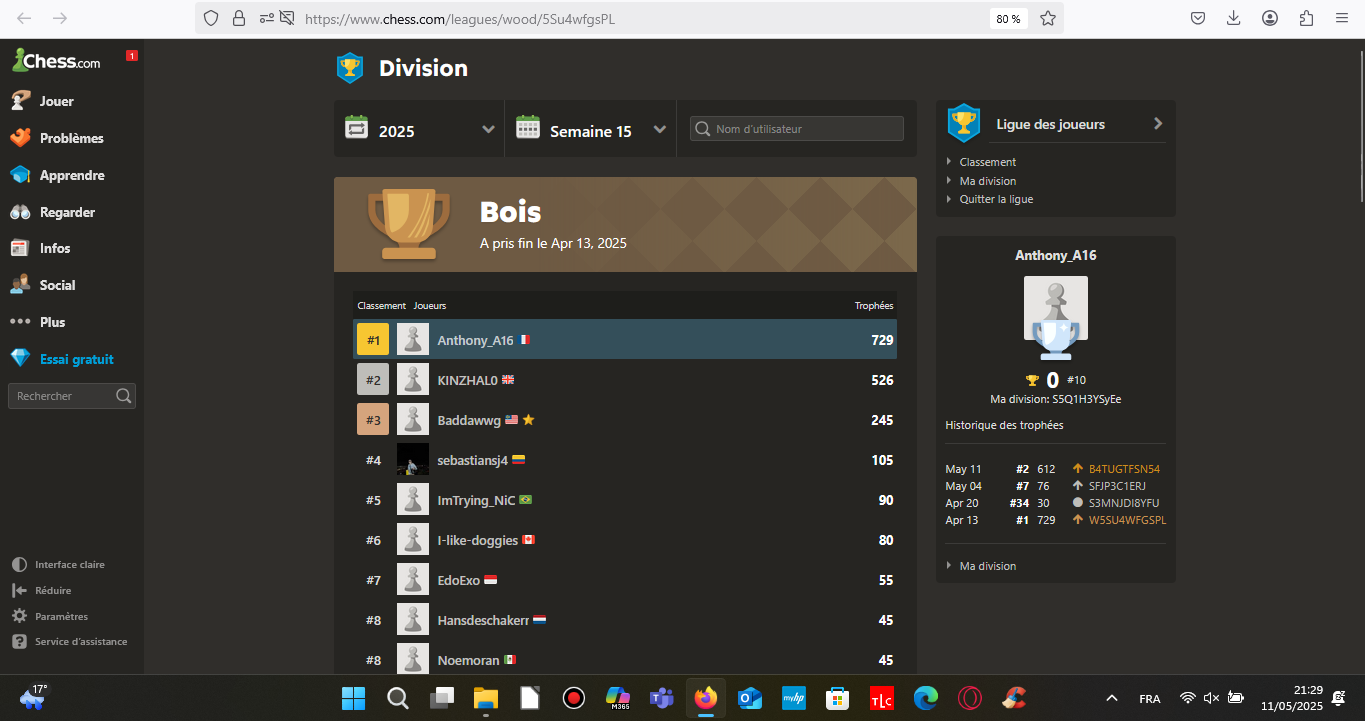
Division de bronze.
 https://www.chess.com/leagues/bronze/4tUGTFsN54
https://www.chess.com/leagues/bronze/4tUGTFsN54
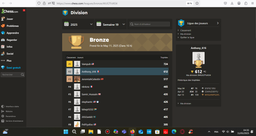
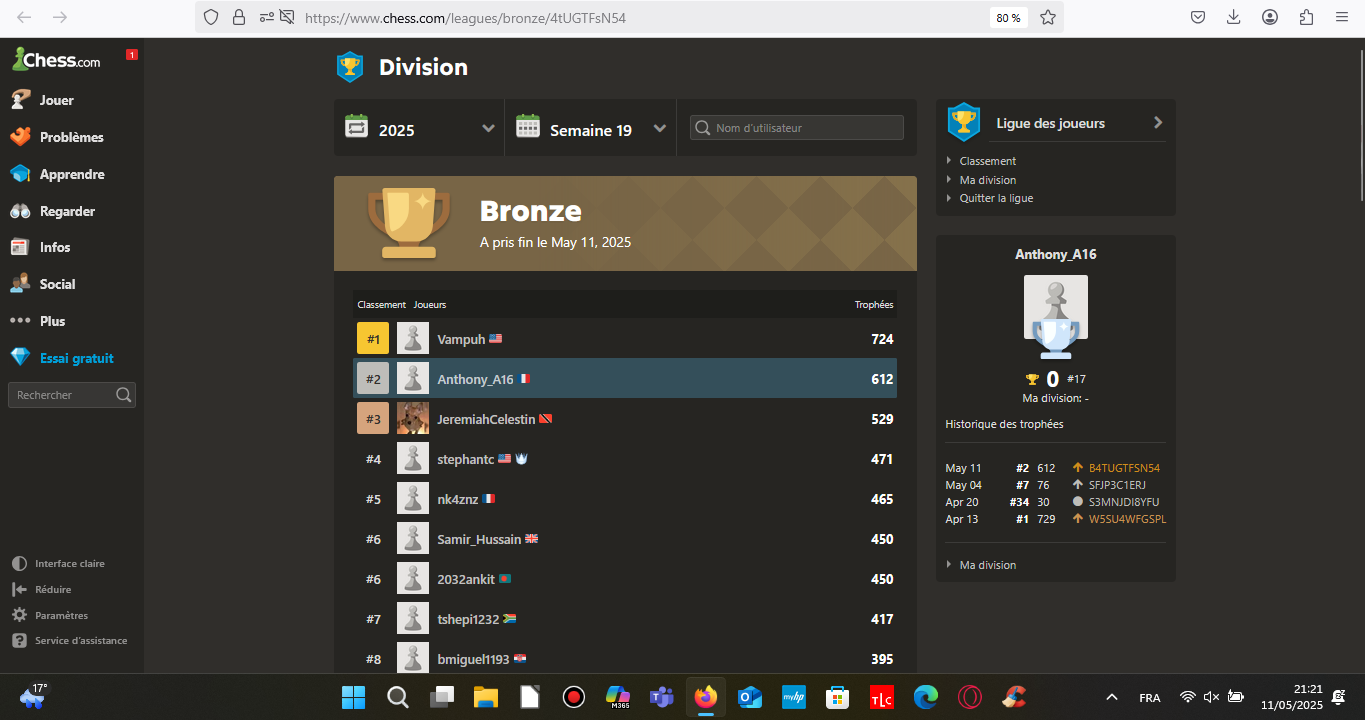
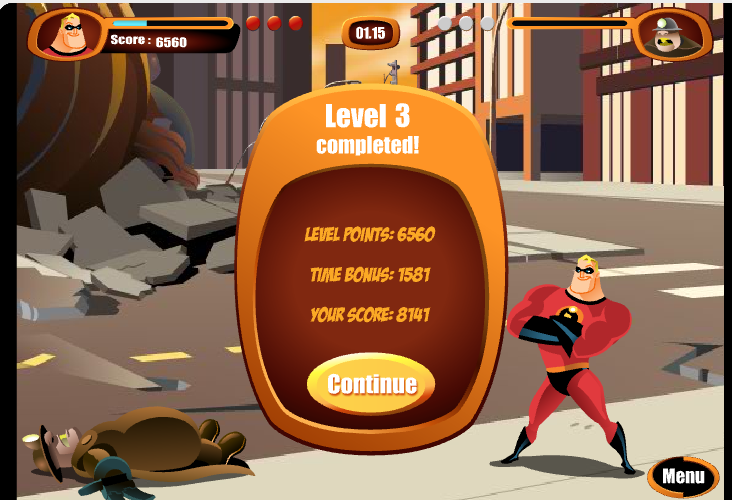
Je termine deuxième.
 https://www.chess.com/game/138362298278
https://www.chess.com/game/138362298278  https://www.chess.com/game/138362327432
https://www.chess.com/game/138362327432  https://www.chess.com/game/138362363270
https://www.chess.com/game/138362363270  https://www.chess.com/game/138362395316
https://www.chess.com/game/138362395316  https://www.chess.com/game/138362428352 Je gagne 5 fois de suite en échecs format 1 minute après avoir été invaincu avec ma précédente série de 4 victoires d'affilée.
https://www.chess.com/game/138362428352 Je gagne 5 fois de suite en échecs format 1 minute après avoir été invaincu avec ma précédente série de 4 victoires d'affilée.
10 mai 2025 : 1, 3 et 10 minutes chess.com 11 mai 2025 : 3 minutes 12 mai 2025 : 1 et 3 minutes.
 https://www.chess.com/leagues/bronze/4tUGTFsN54
https://www.chess.com/leagues/bronze/4tUGTFsN54
 https://www.chess.com/game/138459471704
https://www.chess.com/game/138459471704
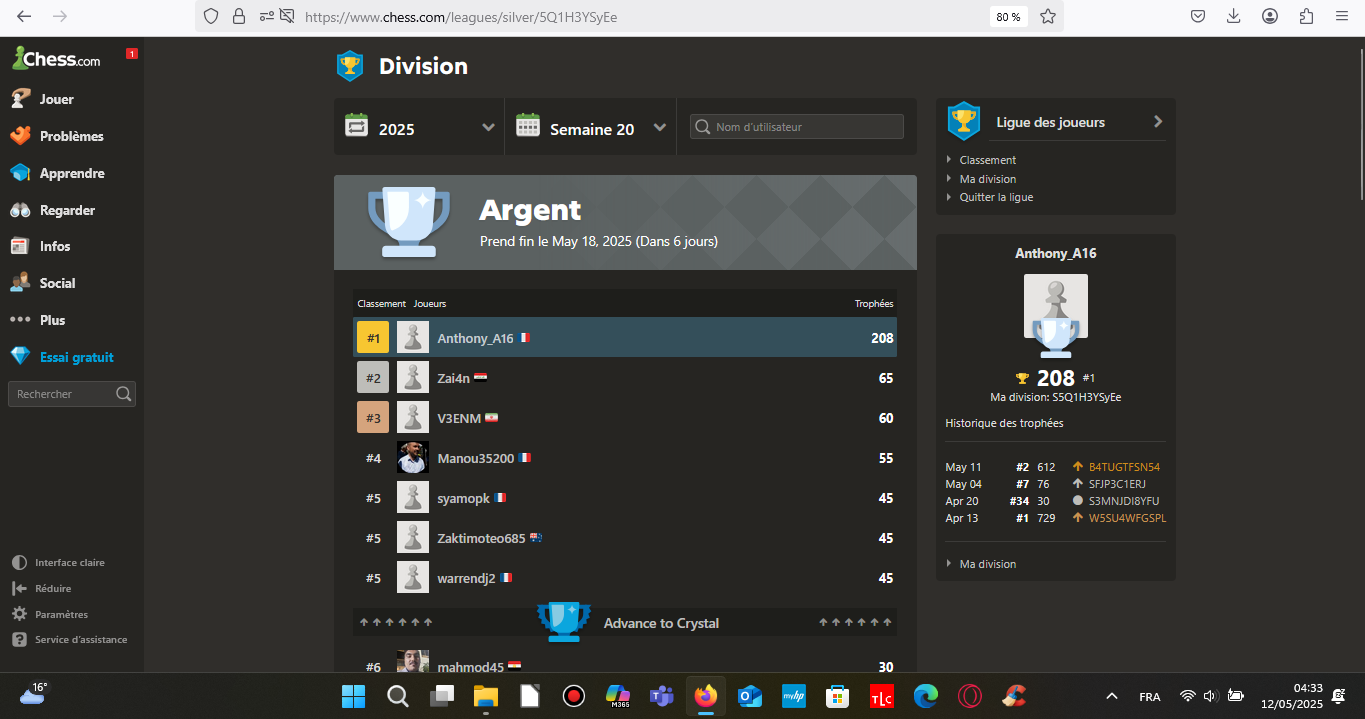
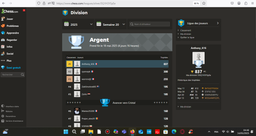
 https://www.chess.com/leagues/silver/5Q1H3YSyEe
https://www.chess.com/leagues/silver/5Q1H3YSyEe
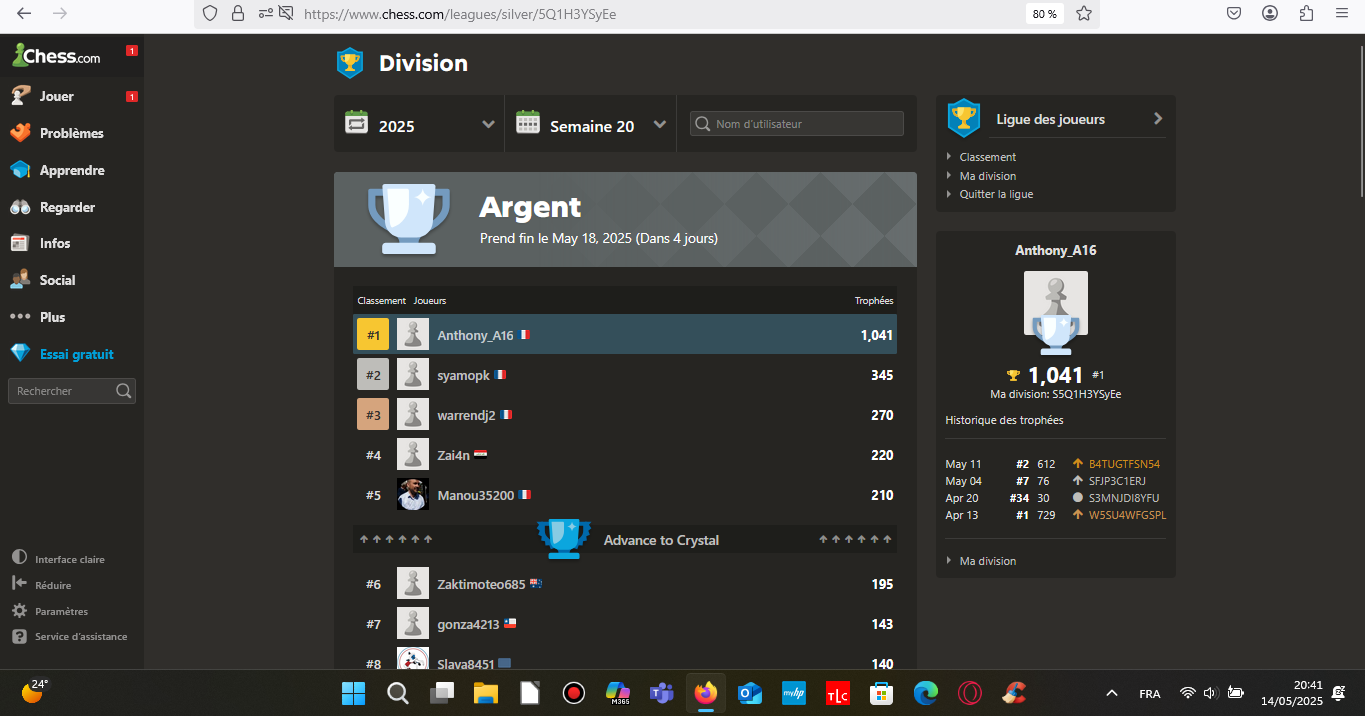
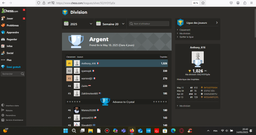
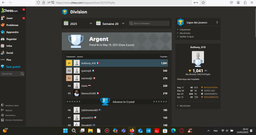
Plus de 1 000 points en moins de 3 jours.
 https://www.chess.com/leagues/silver/5Q1H3YSyEe
https://www.chess.com/leagues/silver/5Q1H3YSyEe
 https://www.chess.com/play/tournament/5691215 tournoi échecs en 10 minutes. Je termine quatrième sur une trentaine.
https://www.chess.com/play/tournament/5691215 tournoi échecs en 10 minutes. Je termine quatrième sur une trentaine.
 https://www.chess.com/leagues/crystal/5dAZw6p5W6
https://www.chess.com/leagues/crystal/5dAZw6p5W6
 https://www.chess.com/leagues/elite/3ogL5BQHNN
https://www.chess.com/leagues/elite/3ogL5BQHNN
1 200 elo en 1 minute bullet.
 https://www.chess.com/leagues/champion/3nEtsesNa2
https://www.chess.com/leagues/champion/3nEtsesNa2
1 000 points elo en blitz 3 minutes
 https://www.chess.com/game/139327568146
https://www.chess.com/game/139327568146

Division de bois.

Division de pierre.
Division de bronze.

Je termine deuxième.
10 mai 2025 : 1, 3 et 10 minutes chess.com 11 mai 2025 : 3 minutes 12 mai 2025 : 1 et 3 minutes.


Plus de 1 000 points en moins de 3 jours.
1 200 elo en 1 minute bullet.
1 000 points elo en blitz 3 minutes
il y a 8 mois
Post. 
This is how Hackers can OWN YOU with just a link!
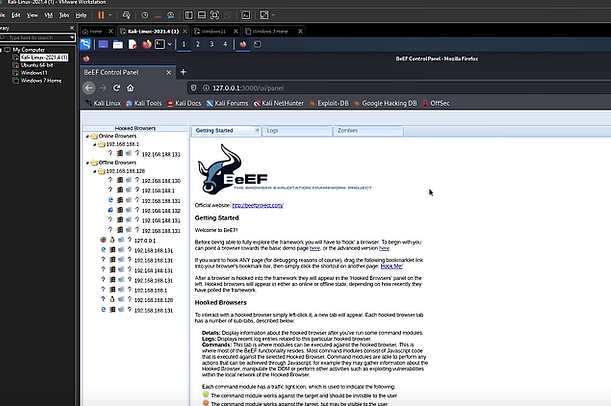
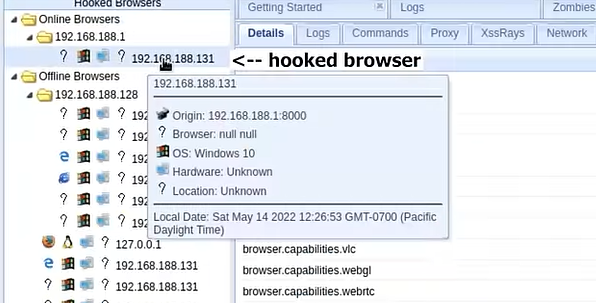
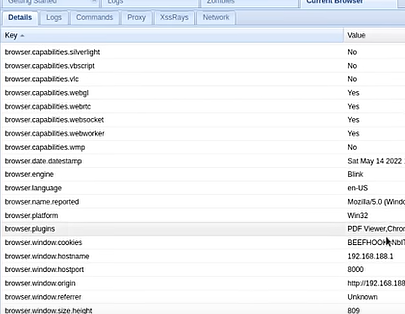
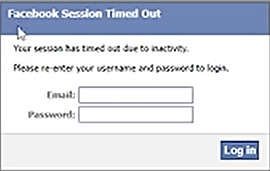
Sometimes, a person can send you a link apparently leading to a trailer, let's say a movie trailer. First it seems like a normal page with a youtube video embedded. I can play the youtube video from this page. But in fact during this time your browser got hooked the hacker's command and control server. So now the hacker can control your browser. From a hacker perspective you can see interface of browser exploitation. Framework, short for BeEF. On the left side you can see the browser that is hooked and right away you see all that information about that browser, like the browser capabilities, IP adress, user agent, time zone, cookies, etc... The javascript on the link clicked on connected itself to the BeEF framework that is running on the hacker's computer. This is actually not a big deal because it's intended functionality of javascript. It creates a way to write instructions that will be executed by the browser. So with BeEF framework I can make someone click on a link that runs some javascript on their browser and then i can connect to this javascript instance from my BeEF control panel. This is called hooking. On the hooker browser; on command tabs different types of command can be executed. When i execute the google pishing module under social engineering you can see the victim's browser that the web page turns a gmail login page like this. It doesn't redirect to a new URL but it changes the content inside the web page. It's a fake gmail page and if you put your credentials here, they are captured and sent to the hacker. So If I come back to my BeEF control panel, I can find the entered credentials Always check if the website has a secure connexion, cross checking the domain name of the website, etc.... Another module in BeEF that will let you know if the hooker browser is logged into any social media like facebook, twitter and gmail. This can be used for enumeration so that the hacker can find out if the victim is logged into any social networking sites and then he can use the " pretty theft " module to show a fake session time out asking for the user's credentials to login again. It's a fake popup and the credential are sent back to the hacker. Something making these browsers attacks worse, it's using an outdated browser. Use a browser regularly maintained and updated. If for example you have a windows 7 vm which has internet explorer 8 installed, it's an outdated browser and microsoft stopped the support for this a long time ago. Hacker can execute a penal that gets the contents inside the user's clipboards. The clipboard data can send sensitive information like passwords and all it takes for a hacker to steal them is to make you click on a link. The contents of your clipboard are now compromised.
This Discord Server Controls my PC (with Malware)!
Someone could ask you to test their game, to download some discord hacking tools or get some crack softwares. When you open this file, for example fortnitehacks, nothing happens at first. The scammer use a discord server If I open up the discord server inside of it my malware bot has been tracking everything you typed in. It's called a key logger. Using the logs from a key logger we can figure out what websites you have been to, what is your username and password for those websites. When I open my compture the malware I download will automatically open itself back up and the hacker will read whatever I am typing. It wil be a clean windows install Then there is another malware Instead of pretending I am going to play let's say neopets, this malware is loaded and nothing seems to happen. But in the scammer's discord server, it's the command and control center, there are channels being generated now inside of these channels, there are things that my goodness you don't want people to have information on in my info page, here can i see my IP adress. Going into the main tab when I go to the file related channel, write : .grab passwords. All the passwords saved in my Chrome browser. If i type .join the bot will join in a voice call. If you try to loook let's say on chrome, asking how to remove a malware the hacker can write : .kill 2 . It doesn't stop at closing programs. I can write : .ls . You can then type .download . And next to .download, type whatever file you want to download.

Sometimes, a person can send you a link apparently leading to a trailer, let's say a movie trailer. First it seems like a normal page with a youtube video embedded. I can play the youtube video from this page. But in fact during this time your browser got hooked the hacker's command and control server. So now the hacker can control your browser. From a hacker perspective you can see interface of browser exploitation. Framework, short for BeEF. On the left side you can see the browser that is hooked and right away you see all that information about that browser, like the browser capabilities, IP adress, user agent, time zone, cookies, etc... The javascript on the link clicked on connected itself to the BeEF framework that is running on the hacker's computer. This is actually not a big deal because it's intended functionality of javascript. It creates a way to write instructions that will be executed by the browser. So with BeEF framework I can make someone click on a link that runs some javascript on their browser and then i can connect to this javascript instance from my BeEF control panel. This is called hooking. On the hooker browser; on command tabs different types of command can be executed. When i execute the google pishing module under social engineering you can see the victim's browser that the web page turns a gmail login page like this. It doesn't redirect to a new URL but it changes the content inside the web page. It's a fake gmail page and if you put your credentials here, they are captured and sent to the hacker. So If I come back to my BeEF control panel, I can find the entered credentials Always check if the website has a secure connexion, cross checking the domain name of the website, etc.... Another module in BeEF that will let you know if the hooker browser is logged into any social media like facebook, twitter and gmail. This can be used for enumeration so that the hacker can find out if the victim is logged into any social networking sites and then he can use the " pretty theft " module to show a fake session time out asking for the user's credentials to login again. It's a fake popup and the credential are sent back to the hacker. Something making these browsers attacks worse, it's using an outdated browser. Use a browser regularly maintained and updated. If for example you have a windows 7 vm which has internet explorer 8 installed, it's an outdated browser and microsoft stopped the support for this a long time ago. Hacker can execute a penal that gets the contents inside the user's clipboards. The clipboard data can send sensitive information like passwords and all it takes for a hacker to steal them is to make you click on a link. The contents of your clipboard are now compromised.
Someone could ask you to test their game, to download some discord hacking tools or get some crack softwares. When you open this file, for example fortnitehacks, nothing happens at first. The scammer use a discord server If I open up the discord server inside of it my malware bot has been tracking everything you typed in. It's called a key logger. Using the logs from a key logger we can figure out what websites you have been to, what is your username and password for those websites. When I open my compture the malware I download will automatically open itself back up and the hacker will read whatever I am typing. It wil be a clean windows install Then there is another malware Instead of pretending I am going to play let's say neopets, this malware is loaded and nothing seems to happen. But in the scammer's discord server, it's the command and control center, there are channels being generated now inside of these channels, there are things that my goodness you don't want people to have information on in my info page, here can i see my IP adress. Going into the main tab when I go to the file related channel, write : .grab passwords. All the passwords saved in my Chrome browser. If i type .join the bot will join in a voice call. If you try to loook let's say on chrome, asking how to remove a malware the hacker can write : .kill 2 . It doesn't stop at closing programs. I can write : .ls . You can then type .download . And next to .download, type whatever file you want to download.
il y a 8 mois
Post. 
THE 3 4 3 IS THE PERFECT FORMATION | Football Tactics
Many being that the modern form of 3 4 3 began to take place in Italy where this formation emerged from the late 1980's and early 1990's In Italian football, the 3 5 2 was already widely used and as a way to make the system more offensive,, ond of the midfielders was pushed forward to the attacking line to overload the opposition's defense. However the great example application of that time came from Spain with Cruyff's Barcelona especially. But unlike the 3 4 3 we see today with central midfielders and 2 wingbacks, Cruyff's 3 4 3 system used a diamond midfield where Guardiola played as an unique deep lying midfielder ahead of the 3 center backs. Years later, another successful version of the 3 4 3 came from AC Milan in the 1998 / 1999 season was implemented and this season, AC Milan won the championship league. Since then we saw a lot of successful teams using 3 4 3 like Conte's Chelsea, Tuchel's Chelsea who won UCL in 2021, Gasperini's Atalanta who won Europa League in 2024, Alonso's Bayer Leverkusen who won both Bundesliga and the German cup in 2024 while also being Europa League 2024 finalists. Starting with the center backs in the initial phases of the attack, the ideal scenario is having one of the center backs having the ability to advance the ball by carrrying the ball forward and for one of them capable to make good vertical passes. It can also be ideal for this back 3 to transform into a back 4, especially when the opposition uses 3 attackers, pressing the 3 center backs. To achieve this, one of the center backs need to be comfortable moving wide and playing in the lateral zones.
First, one of the wingbacks can drop deep as if he is playing as a fullback with the 3 center backs adjusting and the other wingback pushing high The second way is using the goalkepper as an extra player with the 2 wide center backs shifting to the lateral zones while the goalkepper occupy the position of one of the center backs, more centrally alongside the center center back. Finally, a third way consists of one of the 2 central midfielders dropping back tot he back line to fill the space left by a center back. Since it's a system with 3 center backs, a player from another position such as a defensive midfielder or a fullback can be adapted as the third center back to meet these requirements. The 7 others more advanced players can also effectively help the team to move forward. The wingbacks can provide wide outlets. The central midfielders can help creating passing lanes behind the opponent's first line of pressure. The forwards can offer options for long balls behind the defenders or act as a support to receive ground passes and get the ball to the midfielders, using a third man run dynamic. Once the team advances the play, the attacking movement can become more intricate. 4 essential positions for attacking fluidity are the 2 wingbacks and the 2 wide forwards. Combinatinos between these 2 pairs on the flanks needs to be complementary to avoid a redundancy of rolls. Typically the wide forwards play in half spaces which are the intermediate areas between the wide and central channels while the wingbacks are responsible for stretching the field and staying wide. But it's not the only option and what's making 3 4 3 so flexible are the possibilities of inventing new roles for the wingbacks without compromising the team's functionality.
Imagine a team for example lacking fullbacks who can attack down the flank. Since the wingback position doesn't have as many defensive demands as a fullback, a player from another position such as a midfielder can be adapted. Of course the adapted player need to be capable of defending in a back 5. But the defensive demands are still lower than if they were playing as a fullback. In the example of an adapted midfielder playing as a wingback, they wouldn't necessarly need to stay wide during the attacking phases since they have a wide forward nearby who could move out wide in the flank and the adapted midfielder playing like a central midfielder in the offensive phase. Depending on this characteristics this player could also play as a deep lying playmaker, allowing one of the central midfielders more freedom to advance. This alternative would facilitate defensive transitions because of the shorter distances. Another adaptation is to use a forward as a wingback with the player also being capable of acting as the fifth man of the defensive line when the team is dropping into the defense. This happened for exampel with Samuel Lino at Athlético Madrid. These adaptations are easier to make into a 3 4 3 system. Another adjustment can be made with the wide forwards, more skilled in individual plays, or midfielders better suited to play in tight spaces. In the front 3, the central position can be occupied either by a target striker or a false 9. A traditionnal forward can greatly benefit from wide combinations. especially involving the offensive play of the wingbacks and the wingers along with the support of the central midfielders.
A false 9 can also benefit from the spaces this system provides, allowing them to drop deeper in front of the defensive midfielders and create spaces for the wide forwards to make runs behind the defensive line as the formation's structure naturally supports since these players are usually positionned near the center but the flexibility of the system also applies to the defensive phase starting with the high block. Based on the 3 4 3 we would naturally have a large first line with 3 players pressing initially. But with one fewer player than usual in the defensive line, the structure depending on where the team prefers to create pressing zones. For example, if the goal is to force the opponent to play out wide to press them, the team could concentrate more players in the central areas, positionning the 2 central midfielders on different lines and pulling the wingback inside, forming a sort of double diamond behind the front line while leaving the flanks open to fummel the opponent in that direction. Once the opponent moves the ball wide the team could then shift in the ball side trying to compact the area to try to increase pressure. Anotehr approach can be creating more central pressing zones which is naturally harder because the opponent has more directions to escape the pressure but it could result into a dangerous ball recovery since the team would already be in a nearly frontal position. To do this, structure need to be intentinoally kept more spread out to encourage the opponent to play through the middle.
Once they pick that option, the team can try to trap the ball receiver so they don't have much time to react to the created pressure since there is a risk that the opponent might escape the pressing zone . Another approach could be to pull the wingbacks back a little to strenghten the defense. In this case the team needs to drop back while defending open spaces. In a deeper block the most common system in the 3 4 3 is the transformation into a 5 4 1 with the wingbacks dropping back to form a line of 5 alongside the 3 center backs, and the 2 wide forwards dropping back into the second line to create a line of 4 with the 2 central midfielders, leaving one forward higher up. This setup benefits line ups where there are 3 players who aren't expected to contribute much defensively which would be the 3 attackers. In a team playing in a 4 3 3 or 4 2 3 1 for example, it's common to see 1 or even both wide forwards having to drop back deep to protect the flanks. In these systems, wingers become more important defensive pieces, requiring a combative effort in order to avoid overloading a four man defensive line. In a 3 4 3, this demand to the wide forwards can be reduced. In this system it's common to see the wide forwards dropping back just to fill the spaces in this line of 4 without pressuring too much and instead focusing more on cutting off passing lanes and preparing for a potential counter attack.
This is only possible due to the flexibility provided by a back 5 which allows a player to step out without leaving the back line too exposed. For example if the ball enter the mid wide zone, which is usually covered by the wide forward, this could be contained by the advancing wingback moving forward with a more pressing attitude potentially being assisted by the wide forward for a double team. This can happens while the winger from the opposite flank can rest, waiting for a counter attack. However this also may require a lot of defensive work from the 2 central midfielders who would have to cover a large area. Neverless the midfielders would be better protected by the presence of 3 center backs. Since they form a trio, one of them can step up to press the ball receiver without opening up the defensive line too much as 2 players will still covering the spaces.

Many being that the modern form of 3 4 3 began to take place in Italy where this formation emerged from the late 1980's and early 1990's In Italian football, the 3 5 2 was already widely used and as a way to make the system more offensive,, ond of the midfielders was pushed forward to the attacking line to overload the opposition's defense. However the great example application of that time came from Spain with Cruyff's Barcelona especially. But unlike the 3 4 3 we see today with central midfielders and 2 wingbacks, Cruyff's 3 4 3 system used a diamond midfield where Guardiola played as an unique deep lying midfielder ahead of the 3 center backs. Years later, another successful version of the 3 4 3 came from AC Milan in the 1998 / 1999 season was implemented and this season, AC Milan won the championship league. Since then we saw a lot of successful teams using 3 4 3 like Conte's Chelsea, Tuchel's Chelsea who won UCL in 2021, Gasperini's Atalanta who won Europa League in 2024, Alonso's Bayer Leverkusen who won both Bundesliga and the German cup in 2024 while also being Europa League 2024 finalists. Starting with the center backs in the initial phases of the attack, the ideal scenario is having one of the center backs having the ability to advance the ball by carrrying the ball forward and for one of them capable to make good vertical passes. It can also be ideal for this back 3 to transform into a back 4, especially when the opposition uses 3 attackers, pressing the 3 center backs. To achieve this, one of the center backs need to be comfortable moving wide and playing in the lateral zones.
First, one of the wingbacks can drop deep as if he is playing as a fullback with the 3 center backs adjusting and the other wingback pushing high The second way is using the goalkepper as an extra player with the 2 wide center backs shifting to the lateral zones while the goalkepper occupy the position of one of the center backs, more centrally alongside the center center back. Finally, a third way consists of one of the 2 central midfielders dropping back tot he back line to fill the space left by a center back. Since it's a system with 3 center backs, a player from another position such as a defensive midfielder or a fullback can be adapted as the third center back to meet these requirements. The 7 others more advanced players can also effectively help the team to move forward. The wingbacks can provide wide outlets. The central midfielders can help creating passing lanes behind the opponent's first line of pressure. The forwards can offer options for long balls behind the defenders or act as a support to receive ground passes and get the ball to the midfielders, using a third man run dynamic. Once the team advances the play, the attacking movement can become more intricate. 4 essential positions for attacking fluidity are the 2 wingbacks and the 2 wide forwards. Combinatinos between these 2 pairs on the flanks needs to be complementary to avoid a redundancy of rolls. Typically the wide forwards play in half spaces which are the intermediate areas between the wide and central channels while the wingbacks are responsible for stretching the field and staying wide. But it's not the only option and what's making 3 4 3 so flexible are the possibilities of inventing new roles for the wingbacks without compromising the team's functionality.
Imagine a team for example lacking fullbacks who can attack down the flank. Since the wingback position doesn't have as many defensive demands as a fullback, a player from another position such as a midfielder can be adapted. Of course the adapted player need to be capable of defending in a back 5. But the defensive demands are still lower than if they were playing as a fullback. In the example of an adapted midfielder playing as a wingback, they wouldn't necessarly need to stay wide during the attacking phases since they have a wide forward nearby who could move out wide in the flank and the adapted midfielder playing like a central midfielder in the offensive phase. Depending on this characteristics this player could also play as a deep lying playmaker, allowing one of the central midfielders more freedom to advance. This alternative would facilitate defensive transitions because of the shorter distances. Another adaptation is to use a forward as a wingback with the player also being capable of acting as the fifth man of the defensive line when the team is dropping into the defense. This happened for exampel with Samuel Lino at Athlético Madrid. These adaptations are easier to make into a 3 4 3 system. Another adjustment can be made with the wide forwards, more skilled in individual plays, or midfielders better suited to play in tight spaces. In the front 3, the central position can be occupied either by a target striker or a false 9. A traditionnal forward can greatly benefit from wide combinations. especially involving the offensive play of the wingbacks and the wingers along with the support of the central midfielders.
A false 9 can also benefit from the spaces this system provides, allowing them to drop deeper in front of the defensive midfielders and create spaces for the wide forwards to make runs behind the defensive line as the formation's structure naturally supports since these players are usually positionned near the center but the flexibility of the system also applies to the defensive phase starting with the high block. Based on the 3 4 3 we would naturally have a large first line with 3 players pressing initially. But with one fewer player than usual in the defensive line, the structure depending on where the team prefers to create pressing zones. For example, if the goal is to force the opponent to play out wide to press them, the team could concentrate more players in the central areas, positionning the 2 central midfielders on different lines and pulling the wingback inside, forming a sort of double diamond behind the front line while leaving the flanks open to fummel the opponent in that direction. Once the opponent moves the ball wide the team could then shift in the ball side trying to compact the area to try to increase pressure. Anotehr approach can be creating more central pressing zones which is naturally harder because the opponent has more directions to escape the pressure but it could result into a dangerous ball recovery since the team would already be in a nearly frontal position. To do this, structure need to be intentinoally kept more spread out to encourage the opponent to play through the middle.
Once they pick that option, the team can try to trap the ball receiver so they don't have much time to react to the created pressure since there is a risk that the opponent might escape the pressing zone . Another approach could be to pull the wingbacks back a little to strenghten the defense. In this case the team needs to drop back while defending open spaces. In a deeper block the most common system in the 3 4 3 is the transformation into a 5 4 1 with the wingbacks dropping back to form a line of 5 alongside the 3 center backs, and the 2 wide forwards dropping back into the second line to create a line of 4 with the 2 central midfielders, leaving one forward higher up. This setup benefits line ups where there are 3 players who aren't expected to contribute much defensively which would be the 3 attackers. In a team playing in a 4 3 3 or 4 2 3 1 for example, it's common to see 1 or even both wide forwards having to drop back deep to protect the flanks. In these systems, wingers become more important defensive pieces, requiring a combative effort in order to avoid overloading a four man defensive line. In a 3 4 3, this demand to the wide forwards can be reduced. In this system it's common to see the wide forwards dropping back just to fill the spaces in this line of 4 without pressuring too much and instead focusing more on cutting off passing lanes and preparing for a potential counter attack.
This is only possible due to the flexibility provided by a back 5 which allows a player to step out without leaving the back line too exposed. For example if the ball enter the mid wide zone, which is usually covered by the wide forward, this could be contained by the advancing wingback moving forward with a more pressing attitude potentially being assisted by the wide forward for a double team. This can happens while the winger from the opposite flank can rest, waiting for a counter attack. However this also may require a lot of defensive work from the 2 central midfielders who would have to cover a large area. Neverless the midfielders would be better protected by the presence of 3 center backs. Since they form a trio, one of them can step up to press the ball receiver without opening up the defensive line too much as 2 players will still covering the spaces.
il y a 8 mois
Post. 
Jeux.
Watch How Hackers hack your Discord account..
What if instead of choosing a file to download, he sends you an invite to the server and claims that you can get a free nitro by joining the server. When you join the server, the server has apparently a verification process that is to be completed before you can access it. As a part of the verification you are asked to scan a QR code that is generated by the servers bot. So would you scan it with your discord mobile app? As soon as you download and open the file that your friend sent you or scan the innocent QR code to complete the " verification ". First scenario, someone sends you a file and asks you to download it : the file is actually a malicious software or a malware. In the context of discord hacking it's called a token grabber or a token stealer. It steals a particular string that is associated with your discord account called a token grabber. This token is like a randomly generated secret code that gives you access to your discord account. When someone steals your token they also have access to your discord account. When you log into your discord account with your email and password, this card generates a random value called a token and sends it to you as a response to your login. This token enables you to maintain your authentification with the discord server withotu having to send your email and password with every request you send to discord. It's like a session ID maintaining your session on a web app. When you receive this token, your discord desktop app or your web browser depending on where you were using discord will save this token on a local storage so whenever you open discord you will automatically be logged in withotu having to enter your email and password. This token can be used directly for identification. If you look at the source code of this malicious file there are different paths assigned to different discord clients These parts are where your discord token is saved on your local storage depending on which client you are using discord on. When the malware is executed by a victim, it goes through each of these parts and searches for all the files for the extensions DOT log n dot ldb. When it finds these files it uses a regular expression to match a particular pattern based on the match it extracts the token value which is initial actually in an encrypted script. So it passes this encrypted token value into an AES description function along with the key which is also saved in the local storage in a file called local state. Once the token is decrypted it validates. If this token is working, logs into your account with the token and then extracts some information about your account like your saved biling informations which contains your credit card information, information about your multi factor authentification, etc.... Then it finally sends all these stolen details to the hacker and this is done via a discord webhooks.
So the hacker will receive a discord message with all of your details. Once the hacker has your token, it's very easy for them to log into your discord accoutn. The hacker can then writes and automated script to log into your discord account with your token and spread this malware by sending it to all the people in your friends list and all the servers that you join. This means the message you receive which has the malware attachment is now forwarded to all your friends list and to all the servers that you joined. This is how the malware is spead to infect more people. Don't antivirus software detect this and stop this token stealer from running on your computer? Yes. Anti virus softwares including the pre installed windows defender should be able to detect this file as a malware and stops it from executing unless you are somehow tricked into turning your anti virus off. However the hackers use something known as a crypter that hide the malicious behavior of the malware and this enables it to bypass anti virus detections. A crypter encrypts the malicious file. In this case the token stealer with a secret key before creating the malicious executable file when the file is executed, the crypter loads up, decrypts the malicious code using the secret key then loads this malicious code into the memory and executes it directly. This way, anti virus softwares cannot be detect the malicious behavior of the file. And one can easily buy this fully undetectable cryptos from various hacker forums and dark webs forums. All of this can be avoided if you just ignore the message in first place. Don't download any random file into your computer even if it's coming from your best friend. It might be the hacker sending this messsage from your friend's account. Then there is the QRL hacking when you scan with QR code. It's a social engerinnering tactic. used by hackers to exploit the wrong assumption of users that scanning random QR code cannot lead to anything bad. If you go to discord loging page, you can log using your email and password or log in with a QR code. You can scan your generated QR code from your discord mobile app and you will be authenticated withotu having to enter your credentials. A hacker can exploit this by writing a simple script to take over your discord account with QRL URL checking. Firs thte script opens up an automated browser and goes to the discord loging page which generate an unique QR code to log. Next it extracts this QR code from the web page and saves this as an image file. Finally the hacker or the script sends this QR code to you and tricks you into scanning it. So when you scan it it's the hacker who is being logged into your account on this automated browser. Once logged in it's easy to extract the token because the account is in on the hacker's browser. So you can just extract the tokken from that automated browser. Don't scan QR code from untrusted sources.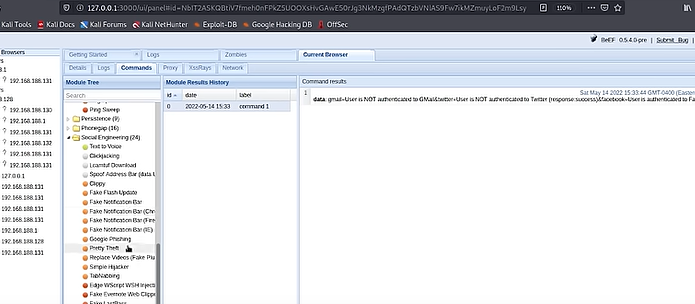

Jeux.







What if instead of choosing a file to download, he sends you an invite to the server and claims that you can get a free nitro by joining the server. When you join the server, the server has apparently a verification process that is to be completed before you can access it. As a part of the verification you are asked to scan a QR code that is generated by the servers bot. So would you scan it with your discord mobile app? As soon as you download and open the file that your friend sent you or scan the innocent QR code to complete the " verification ". First scenario, someone sends you a file and asks you to download it : the file is actually a malicious software or a malware. In the context of discord hacking it's called a token grabber or a token stealer. It steals a particular string that is associated with your discord account called a token grabber. This token is like a randomly generated secret code that gives you access to your discord account. When someone steals your token they also have access to your discord account. When you log into your discord account with your email and password, this card generates a random value called a token and sends it to you as a response to your login. This token enables you to maintain your authentification with the discord server withotu having to send your email and password with every request you send to discord. It's like a session ID maintaining your session on a web app. When you receive this token, your discord desktop app or your web browser depending on where you were using discord will save this token on a local storage so whenever you open discord you will automatically be logged in withotu having to enter your email and password. This token can be used directly for identification. If you look at the source code of this malicious file there are different paths assigned to different discord clients These parts are where your discord token is saved on your local storage depending on which client you are using discord on. When the malware is executed by a victim, it goes through each of these parts and searches for all the files for the extensions DOT log n dot ldb. When it finds these files it uses a regular expression to match a particular pattern based on the match it extracts the token value which is initial actually in an encrypted script. So it passes this encrypted token value into an AES description function along with the key which is also saved in the local storage in a file called local state. Once the token is decrypted it validates. If this token is working, logs into your account with the token and then extracts some information about your account like your saved biling informations which contains your credit card information, information about your multi factor authentification, etc.... Then it finally sends all these stolen details to the hacker and this is done via a discord webhooks.
So the hacker will receive a discord message with all of your details. Once the hacker has your token, it's very easy for them to log into your discord accoutn. The hacker can then writes and automated script to log into your discord account with your token and spread this malware by sending it to all the people in your friends list and all the servers that you join. This means the message you receive which has the malware attachment is now forwarded to all your friends list and to all the servers that you joined. This is how the malware is spead to infect more people. Don't antivirus software detect this and stop this token stealer from running on your computer? Yes. Anti virus softwares including the pre installed windows defender should be able to detect this file as a malware and stops it from executing unless you are somehow tricked into turning your anti virus off. However the hackers use something known as a crypter that hide the malicious behavior of the malware and this enables it to bypass anti virus detections. A crypter encrypts the malicious file. In this case the token stealer with a secret key before creating the malicious executable file when the file is executed, the crypter loads up, decrypts the malicious code using the secret key then loads this malicious code into the memory and executes it directly. This way, anti virus softwares cannot be detect the malicious behavior of the file. And one can easily buy this fully undetectable cryptos from various hacker forums and dark webs forums. All of this can be avoided if you just ignore the message in first place. Don't download any random file into your computer even if it's coming from your best friend. It might be the hacker sending this messsage from your friend's account. Then there is the QRL hacking when you scan with QR code. It's a social engerinnering tactic. used by hackers to exploit the wrong assumption of users that scanning random QR code cannot lead to anything bad. If you go to discord loging page, you can log using your email and password or log in with a QR code. You can scan your generated QR code from your discord mobile app and you will be authenticated withotu having to enter your credentials. A hacker can exploit this by writing a simple script to take over your discord account with QRL URL checking. Firs thte script opens up an automated browser and goes to the discord loging page which generate an unique QR code to log. Next it extracts this QR code from the web page and saves this as an image file. Finally the hacker or the script sends this QR code to you and tricks you into scanning it. So when you scan it it's the hacker who is being logged into your account on this automated browser. Once logged in it's easy to extract the token because the account is in on the hacker's browser. So you can just extract the tokken from that automated browser. Don't scan QR code from untrusted sources.





il y a 8 mois
Post. 
 https://image.noelshack.c[...]ran-2024-09-18-153610.png
https://image.noelshack.c[...]ran-2024-09-18-153610.png
 https://image.noelshack.c[...]ran-2024-09-18-153613.png
https://image.noelshack.c[...]ran-2024-09-18-153613.png
 https://image.noelshack.c[...]ran-2024-09-18-153621.png
https://image.noelshack.c[...]ran-2024-09-18-153621.png
 https://image.noelshack.c[...]ran-2024-09-18-153617.png
https://image.noelshack.c[...]ran-2024-09-18-153617.png
These 6 Discord Scams are EVERYWHERE!
First scam is about a pseudo real account from the actual discord sending you something about nitro. This scam has several things. It has the spread and hooking. First thing is that when you click on the link they want you to add a discord bot to your server. Once it has joined, it sends every person of your server a dm. This scam bot spread all across the discord server. Once the scammer swithces how the bot works when you click on the button it will ask you to authorize an external application to join servers for you. If you authorize this server, scammers can make you join any discrod server that the scam bot is in. To fix that go to authorize apps in your settings and deauthorize nitro to join servers for you. 2. The false verification. Basically you go in a server and they ask you to verify. It could ask you to scan your QR code with your discord mobile app. Don't. Otherwise you sign into the scammer's computer. Second flavor of the scam is that when you click on verify it will tell you to verify yourself to get access to the server. And you need to click here. Click on this link and it's going to take you on a website. It's better to have a VPN in this case. This website is impersonating capture dobot If we go back to discord server and we click on this discord bot, it's supposed to be capture dobot but instead it's verify . On this website it will tell you to press to verify. When you click on press to verify it's going to popup a discord loging page. This is a discord fishing website. Giving your username or email and password you will give it directly to the scammer. If this site on top left is : about:blank it's a scam website. It opens up a new tab to discord and if you aren't logged to discord then it will tell you to log in at the top right. Make sure you are on discord.com for this. Once you log in and go back to discord.com it should tell you to open discord Once you log in and come back to discord.com it should tell you to open discord. It meants your discord accounts is logged in on your browser right now which means if a real website told you to log in it would automatically do it for you. If we refresh the scam website, we click on to press to verify it's not automatically logging me in. What if it's too late and you logged by this way and now your friends are spammed with the same scam? To recover your accoutn then go to your user settings and change your password. Once you change your password it's going to log out every single device on your account. and you are good to go. https://image.noelshack.c[...]ran-2025-03-07-000852.png
https://image.noelshack.c[...]ran-2025-03-07-000852.png
 https://image.noelshack.c[...]ran-2025-03-07-000910.png
https://image.noelshack.c[...]ran-2025-03-07-000910.png
 https://image.noelshack.c[...]ran-2025-03-07-000903.png
https://image.noelshack.c[...]ran-2025-03-07-000903.png
 https://image.noelshack.c[...]ran-2025-03-07-000919.png
https://image.noelshack.c[...]ran-2025-03-07-000919.png
 https://image.noelshack.c[...]ran-2025-03-07-001155.png
https://image.noelshack.c[...]ran-2025-03-07-001155.png
Image
In some occasions if you got scammed by this you might send : 3 : a scam link looking like a steam link. 50 dollars for stream and it's a steam community. This scam is abusing something called discord markdown MK links. With discord you can use formating to turn words into links by just putting it in this format. If you press enter, that link turned just turned into this word. which is now a hyperlink. If I click on it it's going to tell me what website I am going to. For the steam scam when you click on it It's telling you that it's taking you to qptr.ru If you visit the website, it's not a steam community . But it looks like stream and it tells you to get my 50 dollars gift card. Click on this and get the card button. Click on this button and it's taking you to a steam loging page. It seems like a new window but if you try dragging it it doesn't work because this is just part of the website. It will ask you to sign in. Obviously don't do that. Open up a new tab, go to steam community, log in through steam and make sure it's the right website. If you are unsure it's a scam, if you refresh the page if it's a real steam website then you should already be loged in. If you fall for a scam like this things are a bit more difficult to recover There will be this steam support page. Click on the option what if your steam accout is stolen and go through the process. It will tell you to change your password, remove all authenticated devices. 4. This scam tends to talk about struggling artists and people who are giving you thousands of dollars. It's not just one scam but a collection of scams that operate off the same principle. Someone will advertise about their art, telling they are an artist looking for commission to pay let's say a relative's hospital bills. That person will show their " art " mostly stolen or IA generated. They will do art for you for a small fee. Some psychotics might even pretend they know the winning lottery but only in exchange of a few money. Another scam shows someone asking you if you had thousands of ollars deposited and it was deposited in your cash app or paypal. They are going to send you an email not even from paypal but from their email, saying that major finance company sent you thousands. They will say you just have to pay 100 of tax fee before the money is available in yout account. This is obviously a scam.
. https://image.noelshack.c[...]ran-2025-03-07-001949.png
https://image.noelshack.c[...]ran-2025-03-07-001949.png
 https://image.noelshack.c[...]ran-2025-03-07-002002.png
https://image.noelshack.c[...]ran-2025-03-07-002002.png
 https://image.noelshack.c[...]ran-2025-03-07-001956.png
https://image.noelshack.c[...]ran-2025-03-07-001956.png
 https://image.noelshack.c[...]ran-2025-03-07-002145.png
https://image.noelshack.c[...]ran-2025-03-07-002145.png
 https://image.noelshack.c[...]ran-2025-03-07-002444.png
https://image.noelshack.c[...]ran-2025-03-07-002444.png
 https://image.noelshack.c[...]ran-2025-03-07-002331.png
https://image.noelshack.c[...]ran-2025-03-07-002331.png
.















First scam is about a pseudo real account from the actual discord sending you something about nitro. This scam has several things. It has the spread and hooking. First thing is that when you click on the link they want you to add a discord bot to your server. Once it has joined, it sends every person of your server a dm. This scam bot spread all across the discord server. Once the scammer swithces how the bot works when you click on the button it will ask you to authorize an external application to join servers for you. If you authorize this server, scammers can make you join any discrod server that the scam bot is in. To fix that go to authorize apps in your settings and deauthorize nitro to join servers for you. 2. The false verification. Basically you go in a server and they ask you to verify. It could ask you to scan your QR code with your discord mobile app. Don't. Otherwise you sign into the scammer's computer. Second flavor of the scam is that when you click on verify it will tell you to verify yourself to get access to the server. And you need to click here. Click on this link and it's going to take you on a website. It's better to have a VPN in this case. This website is impersonating capture dobot If we go back to discord server and we click on this discord bot, it's supposed to be capture dobot but instead it's verify . On this website it will tell you to press to verify. When you click on press to verify it's going to popup a discord loging page. This is a discord fishing website. Giving your username or email and password you will give it directly to the scammer. If this site on top left is : about:blank it's a scam website. It opens up a new tab to discord and if you aren't logged to discord then it will tell you to log in at the top right. Make sure you are on discord.com for this. Once you log in and go back to discord.com it should tell you to open discord Once you log in and come back to discord.com it should tell you to open discord. It meants your discord accounts is logged in on your browser right now which means if a real website told you to log in it would automatically do it for you. If we refresh the scam website, we click on to press to verify it's not automatically logging me in. What if it's too late and you logged by this way and now your friends are spammed with the same scam? To recover your accoutn then go to your user settings and change your password. Once you change your password it's going to log out every single device on your account. and you are good to go.
Image
In some occasions if you got scammed by this you might send : 3 : a scam link looking like a steam link. 50 dollars for stream and it's a steam community. This scam is abusing something called discord markdown MK links. With discord you can use formating to turn words into links by just putting it in this format. If you press enter, that link turned just turned into this word. which is now a hyperlink. If I click on it it's going to tell me what website I am going to. For the steam scam when you click on it It's telling you that it's taking you to qptr.ru If you visit the website, it's not a steam community . But it looks like stream and it tells you to get my 50 dollars gift card. Click on this and get the card button. Click on this button and it's taking you to a steam loging page. It seems like a new window but if you try dragging it it doesn't work because this is just part of the website. It will ask you to sign in. Obviously don't do that. Open up a new tab, go to steam community, log in through steam and make sure it's the right website. If you are unsure it's a scam, if you refresh the page if it's a real steam website then you should already be loged in. If you fall for a scam like this things are a bit more difficult to recover There will be this steam support page. Click on the option what if your steam accout is stolen and go through the process. It will tell you to change your password, remove all authenticated devices. 4. This scam tends to talk about struggling artists and people who are giving you thousands of dollars. It's not just one scam but a collection of scams that operate off the same principle. Someone will advertise about their art, telling they are an artist looking for commission to pay let's say a relative's hospital bills. That person will show their " art " mostly stolen or IA generated. They will do art for you for a small fee. Some psychotics might even pretend they know the winning lottery but only in exchange of a few money. Another scam shows someone asking you if you had thousands of ollars deposited and it was deposited in your cash app or paypal. They are going to send you an email not even from paypal but from their email, saying that major finance company sent you thousands. They will say you just have to pay 100 of tax fee before the money is available in yout account. This is obviously a scam.
.
.
il y a 8 mois
Post. 
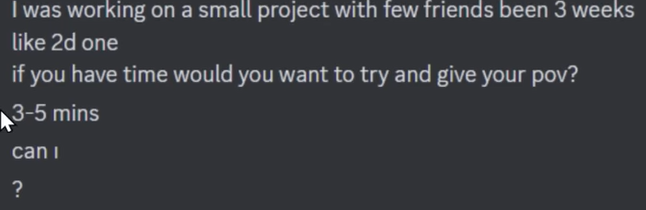
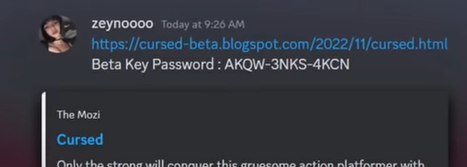
5 : the report scam. A person will say they accidentally reported you several times. They might say they got hacked on discord and they thought it was you who hacked them because the hacker and you have a similar profile picture. and since that's the case they accidentally filed a whole bunch of tickets on your account, meaning you are going to get banned. And they send you a photo of this email.In this email if you read it it will be obvious that's a scam. He will send a link where to contact discord support to not be banned. You will see there is no discord staff badge which is another massive red flag. But if you had the fake support discord they will show you that they really work at discord with a professionnal certificate. There is usually a link to their actual linkedin. Often it will say data scientist but generally a data scientist won't do trust and safety so it's another red flag. Scammers will copy all informations of this linkedin and put it in these fake resumes to try to look real. If you get trouble on discrod normally you either get a message from discord either you will receive a email from them. Assuming you don't know that these scammers will ask you to change your email with one of their emails that your accoutn will be apparently under discord's protection custody report. They will manipulate you into getting to your settings and to change your email. If you do, they will have full access to your account. They can go to nitro tab and buy a whole bunch of nitro or sell the discord nitro to make money. With multi factor identification if you change your mail they can't change your password. Add 2 factors identification to your discord account. But the scammers will still have their email on your account. You can't change it back. They will try to extort you out of your money. They will tell you that if you want your discord back, you will have to give them some money. Go to the description of discord's white page of doom and gloom. Enter your username, email and email associated with the accoutn before it was compromised. Put down the email that you had before you changed it to the scammer's email. If the scammers bought a lot of nitro during this time in the what can we help you with section, put" billing. " https://support.discord.c[...]ket_form_id=4574398270487 6 : download my game scam. Some scammers or your friends accoutns that got hacked willl send you a message asking you to help them on their small little project, asking you to test their little game. They might say that they will pay you for every hour you play. And that the payment will be higher if you find bugs or errors in this game. They want you to go on a website and download their game. These scammers are most of the time so lazy that they just impersonate other games that already exist. If you download and open the file it will steal your usernames and passwords + cryptocurrency from your computer and then hide themselves from the computer so even if you change your passwords the new password will be sent to the scammer because the malware is still on your computer. First thing to do is a frehs install of your OS to get rid of your malware. This will delete all of your files When you have a fresh new computer, change every single one of your passwords. Change all the accounts passwords you have on the internet even if you have hundreds of them.
https://support.discord.c[...]ket_form_id=4574398270487 6 : download my game scam. Some scammers or your friends accoutns that got hacked willl send you a message asking you to help them on their small little project, asking you to test their little game. They might say that they will pay you for every hour you play. And that the payment will be higher if you find bugs or errors in this game. They want you to go on a website and download their game. These scammers are most of the time so lazy that they just impersonate other games that already exist. If you download and open the file it will steal your usernames and passwords + cryptocurrency from your computer and then hide themselves from the computer so even if you change your passwords the new password will be sent to the scammer because the malware is still on your computer. First thing to do is a frehs install of your OS to get rid of your malware. This will delete all of your files When you have a fresh new computer, change every single one of your passwords. Change all the accounts passwords you have on the internet even if you have hundreds of them.


This Discord Predator is Disgusting...
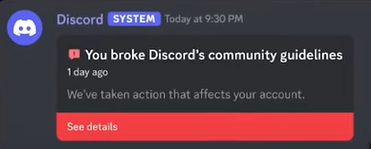
There were complaints on August 2022 that a guy named Rabid on discord was grooming minor to create child pornography and engage in self harm. The FBI identified Rabid as Densmore. Since he got arrested in 2024, the FBI knew about him being a pedophile for 2 years. One of the victim, 15 years back then reported to investigators that she knew Rabid's first name was Richard and that he created a discord server called " Sewer " to stream child pornography and self harm content. The girl streamed a video of herself on Sewer in which she inserted an ice cube into her vagina. When FBI investigated the Rabid guy they also found things related to 764 cult. Somehow after 11 months, Densmore was a free man. Eventually he got arrested and jailed. Densmore was a 47 years old with mental trouble who used to serve in the US military. He had on his phone photos of people hurting themselves. He also had guns, ammunitions and other weapons on his house. However judge Kent denied governemnt's request for pretrial detention, even releasing him with 10 000 dollars unsecured bond. And it was on February 2024. A legal document was made on March 2025 with a plea agreement. If Richard signed the plea deal he would basically admit he is guilty.
.
Big Discord Servers are Getting Hacked!
How did Beluga discord server got hacked? Rand. One of the Beluga servers admins fell for social engineering trick that compromised their discord account. You might if you got victim os such hack, be banned from random servers. These hackers try to impersonate you and make fake message transaction to shit on your reputation. They sent this to the Valorant server to get Rand banned. Once you got banned the hackers can impersonate a particular admin asking if you want to appeal. When you say it wasn't you who did the things that got you banned they might say that they don't believe you then they could get you to do a screen recording or get you to join a little voice call with them. You could have to talk to a certain Pee6 to proof innocent. They get you to click on a message thing. Opening up this console thing is a no go zone. They will probably try to compromise your account. Anyone on your console can get your token. If you go to the local storage there is a token that they could get from you to try to compromise your account. Now that's screen recorded and when you send your screen recording back to proof innocence they will grab your discord token and log into your account. Whenever you think someone has your discord token, go to your user settings, scroll down and change your password. Since you changed your password it should reset your token. You can also go to your devices and get rid of any device that you don't recognize.






5 : the report scam. A person will say they accidentally reported you several times. They might say they got hacked on discord and they thought it was you who hacked them because the hacker and you have a similar profile picture. and since that's the case they accidentally filed a whole bunch of tickets on your account, meaning you are going to get banned. And they send you a photo of this email.In this email if you read it it will be obvious that's a scam. He will send a link where to contact discord support to not be banned. You will see there is no discord staff badge which is another massive red flag. But if you had the fake support discord they will show you that they really work at discord with a professionnal certificate. There is usually a link to their actual linkedin. Often it will say data scientist but generally a data scientist won't do trust and safety so it's another red flag. Scammers will copy all informations of this linkedin and put it in these fake resumes to try to look real. If you get trouble on discrod normally you either get a message from discord either you will receive a email from them. Assuming you don't know that these scammers will ask you to change your email with one of their emails that your accoutn will be apparently under discord's protection custody report. They will manipulate you into getting to your settings and to change your email. If you do, they will have full access to your account. They can go to nitro tab and buy a whole bunch of nitro or sell the discord nitro to make money. With multi factor identification if you change your mail they can't change your password. Add 2 factors identification to your discord account. But the scammers will still have their email on your account. You can't change it back. They will try to extort you out of your money. They will tell you that if you want your discord back, you will have to give them some money. Go to the description of discord's white page of doom and gloom. Enter your username, email and email associated with the accoutn before it was compromised. Put down the email that you had before you changed it to the scammer's email. If the scammers bought a lot of nitro during this time in the what can we help you with section, put" billing. "








There were complaints on August 2022 that a guy named Rabid on discord was grooming minor to create child pornography and engage in self harm. The FBI identified Rabid as Densmore. Since he got arrested in 2024, the FBI knew about him being a pedophile for 2 years. One of the victim, 15 years back then reported to investigators that she knew Rabid's first name was Richard and that he created a discord server called " Sewer " to stream child pornography and self harm content. The girl streamed a video of herself on Sewer in which she inserted an ice cube into her vagina. When FBI investigated the Rabid guy they also found things related to 764 cult. Somehow after 11 months, Densmore was a free man. Eventually he got arrested and jailed. Densmore was a 47 years old with mental trouble who used to serve in the US military. He had on his phone photos of people hurting themselves. He also had guns, ammunitions and other weapons on his house. However judge Kent denied governemnt's request for pretrial detention, even releasing him with 10 000 dollars unsecured bond. And it was on February 2024. A legal document was made on March 2025 with a plea agreement. If Richard signed the plea deal he would basically admit he is guilty.
.
How did Beluga discord server got hacked? Rand. One of the Beluga servers admins fell for social engineering trick that compromised their discord account. You might if you got victim os such hack, be banned from random servers. These hackers try to impersonate you and make fake message transaction to shit on your reputation. They sent this to the Valorant server to get Rand banned. Once you got banned the hackers can impersonate a particular admin asking if you want to appeal. When you say it wasn't you who did the things that got you banned they might say that they don't believe you then they could get you to do a screen recording or get you to join a little voice call with them. You could have to talk to a certain Pee6 to proof innocent. They get you to click on a message thing. Opening up this console thing is a no go zone. They will probably try to compromise your account. Anyone on your console can get your token. If you go to the local storage there is a token that they could get from you to try to compromise your account. Now that's screen recorded and when you send your screen recording back to proof innocence they will grab your discord token and log into your account. Whenever you think someone has your discord token, go to your user settings, scroll down and change your password. Since you changed your password it should reset your token. You can also go to your devices and get rid of any device that you don't recognize.
il y a 8 mois
